Public Key Encryption Definition Computer Science
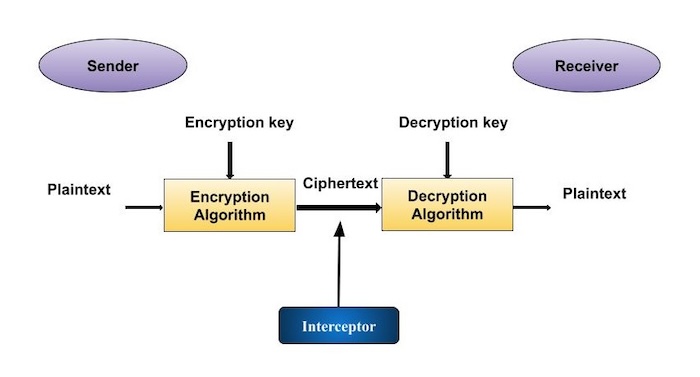
Public-key encryption is a cryptographic system that uses two keys a public key known to everyone and a private or secret key known only to the recipient of the message. Tlie encryption method is said to be a public-key encryption scheme if for each associated encryptiondecryption pair e d one key e the public key is made publicly available while the other d the private key is kept secret.

Public Key Encryption An Overview Sciencedirect Topics
Mia Epner who works on security for a US national intelligence agency explains how cryptography allows for the secure transfer of data online.
Public key encryption definition computer science. They can also be useful as initialization vectors and in cryptographic hash functions. Lets step through the high-level process of public key encryption. One way around this issue is to use an algorithm that.
Public key encryption to the rescue. The other key is known as the private key. Public key encryption also referred to as asymmetric cryptography replaced the one shared key with each users own pair of keys.
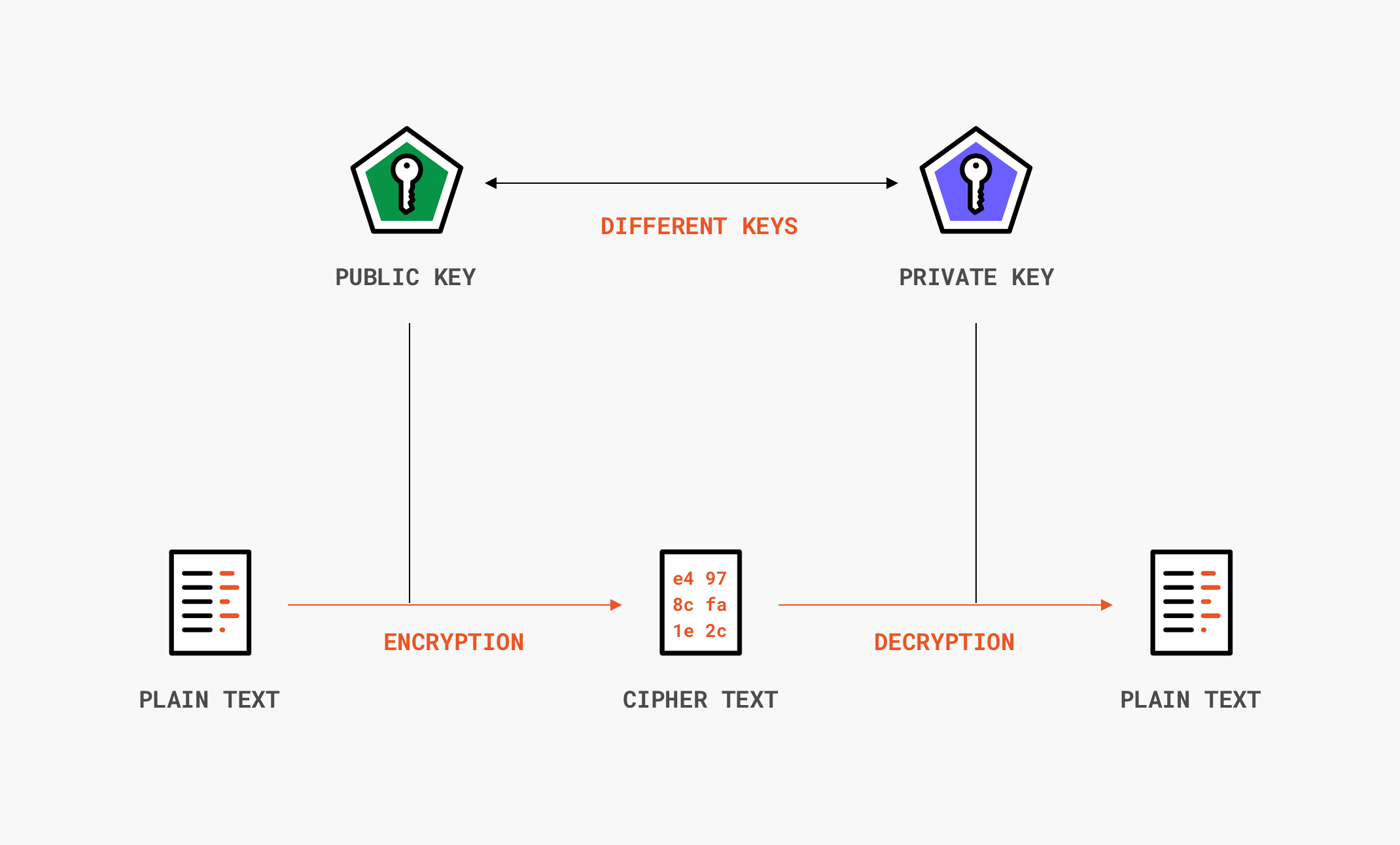
A public key and a private secret key. One key is a public key which is made available to everyone and is used for the encryption process only. When John wants to send a secure message to Jane he uses Janes public key to.
Like all methods of disguise encryption is of little use if unauthorised users know the key. It is similar in spirit to a nonce word hence the name. Public key encryption or public key cryptography is a method of encrypting data with two different keys and making one of the keys the public key available for anyone to use.
Only with the matching personal key will a message encode with the common key be decoded. Alice has a public key a private key and an encryption method. The key can be generated by a software program but more often it is provided by a trusted designated authority and made available to everyone through a publicly accessible repository or directory.
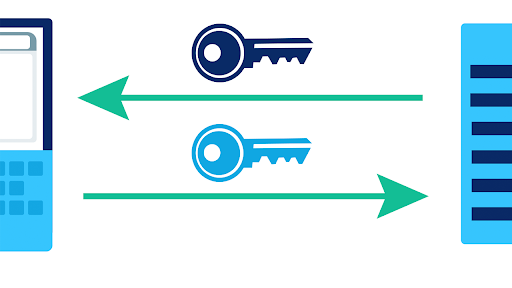
They can use it to unlock any message that is encrypted with that key. Public key systems One of the remarkable discoveries in computer science in the 1970s was a method called public key encryption where its fine to tell everyone what the key is to encrypt any messages but you need a special private key to decrypt it. Because Alice and Bob use different keys this is called an asymmetric encryption system.
To encrypt the public key is applied to the target. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused in replay attacks. In contrast to the symmetric system asymmetric public-key crypto uses two different keys.
One way around this issue is to. Encryption is of little use if unauthorised users know the key. Public key encryption is a form of encryption that uses two keys.
The other key in the pair the private key is available only to the owner. This video explains 256-bit encryption public and private keys SSL TLS and HTTPS. Asymmetric encryption is a type of data cipher also called a public-key cipher where the cipher key also known as the common key and one the other side decode key also known as the personal key vary.
Mia Epner who works on security for a US national intelligence agency explains how cryptography allows for the secure transfer of data online. Public-key cryptography has three players generally called Alice Bob and the Adversary. Its an asymmetric encryption technique which uses different keys for encryption and decryption allowing computers over the Internet to securely communicate with each other.
They can use it to decrypt any message that is encrypted with that key. In cryptography a public key is a large numerical value that is used to encrypt data. A public key which everyone knows and a private key which only you know.

Encryption Protocols What They Are How They Work Venafi
Public Key Encryption Article Khan Academy

Secret Key An Overview Sciencedirect Topics

Public Key Cryptography An Overview Sciencedirect Topics
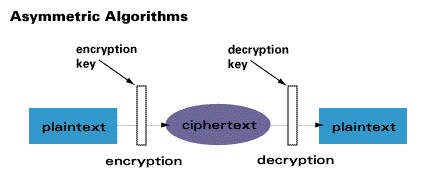
Cryptography Defined Brief History
Encryption And Public Keys Video Khan Academy

Public Key Encryption An Overview Sciencedirect Topics

Symmetric Encryption Definition Example Video Lesson Transcript Study Com
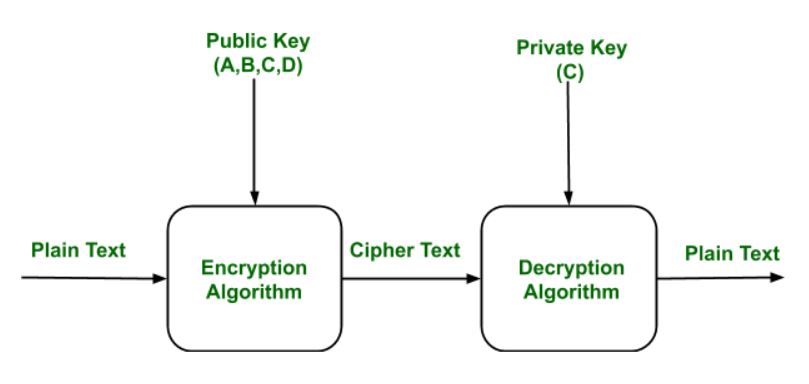
Public Key Encryption Geeksforgeeks

Symmetric Encryption Cryptography In Java Geeksforgeeks
What S The Difference Between Encryption Hashing Encoding And Obfuscation
Asymmetric Encryption Simply Explained Youtube

Public Key Algorithm An Overview Sciencedirect Topics
Public Key Encryption Article Khan Academy

Symmetric Encryption Definition Example Video Lesson Transcript Study Com
Asymmetric Encryption Types Examples Facts

Public Key Encryption Tutorialspoint

Si110 Asymmetric Public Key Cryptography

Post a Comment for "Public Key Encryption Definition Computer Science"